Before a company sale can take place, investors participate in a financing round, or a stock exchange listing can be considered, the matter of due diligence must be dealt with first.
Information security is one of the core topics of due diligence audits. How information security should be managed is defined in the international ISO 27001 standard. In this article, we explain what it means and what businesses should take note of throughout its implementation.
What you need to know, in a nutshell
- During a due diligence process, the information security of the company in question is also put under the microscope.
- Information security encompasses much more than just IT security: It also includes the processes and the people within the company.
- ISO 27001 formulates requirements towards information security management systems (ISMS).
- Companies with ISO 27001 certification are highly trusted, which increases their value as a business. For these organisations, due diligence can be significantly more compact.
- For service providers and suppliers in the automotive industry, TISAX approval is the equivalent of ISO 27001 certification.
In this article
- What does due diligence mean? When do companies have to carry this process out?
- What does a due diligence process look at? Who examines whom?
- The benchmark for information security is ISO 27001. What does this standard mean?
- What is an information security management system (ISMS)?
- What are the advantages of a certified ISMS?
- TISAX acts as the automotive industry’s own standard – why?
- TISAX and ISO 27001 have a risk-based approach: What does that mean?
- What is the conclusion?
What does due diligence mean? When do companies have to carry out such a process?
The literal meaning of ‘due diligence’ is to take the care required. This term is used to describe a process for examining the statements and information a company provides regarding the value of its business and the risks involved. A due diligence audit is carried out when an investor or purchaser is interested in a company, or before a stock market launch. Anybody who is planning to invest in or take over a company wants to be sure that the statements made about a company and their future collaboration reflect reality.
What does a due diligence process look at? Who examines whom?
The audit is generally carried out by specialist corporate lawyers or business consultants. What is audited depends on the risk exposure in that particular case. Beyond US investor protection legislation, there are no binding standards for due diligence. The minimum action required is a complete audit of the company accounts. However, many other areas are generally examined as well, such as all the company’s relevant processes, its asset values and liabilities, existing contracts with employees, partners and suppliers, compliance, product development standards, supply chain security, and communications and information security. Assessing the latter is very complicated and requires specialist knowledge. DataGuard makes this knowledge accessible via a SaaS platform, offering an auditing solution for information security and the development of individual, optimised information security management systems (ISMS).
The benchmark for information security is ISO 27001. What does this standard mean?
To make it clear, the term information security means and describes much more than just the IT security of a company. This is because, in addition to the technical equipment, the security of all processes and business activities of a company are in the limelight, as well as the qualifications and trustworthiness of the people involved – including not only the workforce and the management, but also the suppliers. It therefore covers a very broad spectrum, which we have illustrated below:
|
Let’s look at business continuity management as an example:
There are two companies.Both offer software-as-a-service products via a cloud.The products therefore require a functioning cloud.When auditing the information security in accordance with ISO 27001, the following questions need to be asked in particular: Which cloud service providers are the companies using, how high is the probability of a technical failure, how severe would this be and what effects could it have on the business activities, and what measures have been taken for this eventuality? The answers may be very different.
Company A) Let’s assume that Company A offers a SaaS product for automatic time recording. The probability of a failure is very low.However, if there was a malfunction, customers would have to log their times temporarily on a spreadsheet or by hand and enter them in the software manually later.That would be annoying, but the damage would be negligible.
Company B) It is a different case for Company B. This company offers a SaaS automated stock trading product via the cloud.If there is an outage, not only could it be bothersome, but it could cause high financial losses, not to mention considerable reputational damage with long-term consequences.The risk would be considerably higher. Suitably thorough protective measures would have to be defined within an information security management system (ISMS) in accordance with ISO 27001.
The international ISO 27001 standard currently does not contain any instructions that state how this task should be organised in each individual case. The standard only specifies in which areas and with which objectives an assessment and treatment of the risks must take place. The company itself must gauge how in-depth an audit should sensibly be.
What is an information security management system (ISMS)?
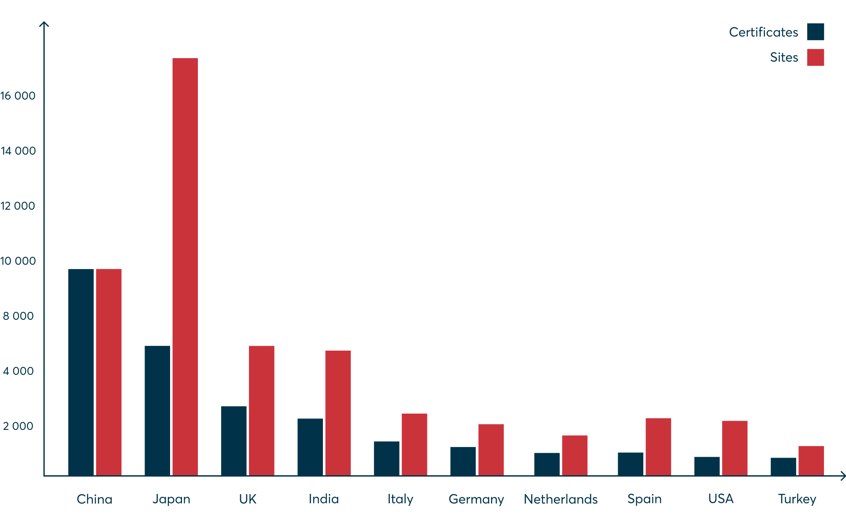
An ISMS defines rules, methods, and measures to manage the information security of an organisation. Its implementation is individual and takes place for the respective organisation as a whole, on a process-orientated basis. The international ISO 27001 standard, therefore, provides globally uniform guidelines for the development and operation of an ISMS. If these guidelines are followed verifiably and demonstrably, a company can have its own ISMS certified accordingly. What is interesting is that most ISO 27001 ISMS certificates by far are issued in China.
What are the advantages of a certified ISMS?
Companies that have a certified management system for their information security benefit in more ways than one, particularly because they can systematically detect and minimise risks to their IT, business activities, processes, and finally, the behaviour of the people within their organisations. An ISMS ensures the right behaviour; potential hazards are eliminated – for example, by introducing end-to-end encryption of data in the cloud – and response plans are developed for any security breaches that may happen.
In other words, companies with a certified ISMS have excellent risk management in regards to information security. This increases the trust of the customers and potential partners/interested parties in the performance of the company, giving it both an important competitive edge in the market. Depending on the industry, a certified ISMS also acts as proof that the company is fulfilling its compliance requirements and other legal requirements, such as those that apply to operators of critical infrastructures.
What we can be certain about is that the investment and costs of certification pay off in any case – especially when a due diligence audit is planned: Such audits are considerably easier and therefore faster when the company is already ISO 27001 certified. This shortens the process and often increases the value of the company considerably.
TISAX acts as the automotive industry’s own standard – why?
TISAX stands for Trusted Information Security Assessment Exchange. It is a separate standard developed by the Verband der Automobilindustrie (German Association of the Automotive Industry). The TISAX guidelines are based directly on ISO 27001. They are somewhat less extensive, but they have been specially adjusted to the requirements of the automotive industry and are aimed explicitly at the service providers and suppliers used by manufacturers. Car manufacturers expect their business partners to undergo regular audits and certification as part of an information security assessment (ISA). In addition to the ISA requirements catalogue, TISAX 2017 has also created a mechanism for the reliable exchange of assessment results. The transparency thereby guarantees preventing unnecessary cross-checking. The assessment results are recognised industry-wide, enabling new supplier relationships to be established, and saving lots of time and money.
TISAX and ISO 27001 have a risk-based approach – what does that mean?
The assessment and optimisation of information security in both regulatory systems do not take place based on absolute specifications. As a result, it is not stated in writing what a company has to do to increase its information security. Only the path to the objective is defined, which is always reached by carefully considering the risks your company is exposed to, their probability of occurrence, and the damage they could potentially cause. Those who know the answers to these questions can (and must) introduce and implement proportionate risk management measures.
Let’s take HR security as an example: What risks could a corrupt employee pose? What damage could they potentially cause? Once again, the answers will differ greatly. If we are talking about somebody who works for a national intelligence agency, the disclosure of secrets could have severe diplomatic implications. The risks would be enormous, so the barriers and security measures in the recruitment process would have to be accordingly high. In order to check the suitability of an applicant’s character, a criminal record check alone would not be enough. In contrast, requiring such a certificate from somebody who wants to work in a pasta factory would be unreasonable and in no way productive.
Risk, damage potential and risk-minimising measures must therefore always be applied in a way which is individual, optimal and proportionate. In the future, this can be achieved in a very efficient and resource-effective way using the risk management model provided by DataGuard’s new ISMS platform.
What is the conclusion?
Companies with a certified management system for information security in accordance with ISO 27001 or TISAX are trusted to the highest level and enjoy a decisive competitive edge on the market. These certifications will also increase the value of your company, especially in terms of the due diligence process, and drastically shorten the time taken to perform due diligence. This will save costs enormously and increase the negotiating power of companies that are looking for new partners or investors.
Learn how DataGuard's corporate compliance solutions support ISO 27001 certification for enhanced due diligence.