Effective risk management is critical for companies of all sizes, especially for small businesses looking to navigate a competitive environment. One of the best and widely recognised frameworks for managing information security risks is ISO 27001.
This article explores the topics discussed in our recent ISO 27001 risk management webinar, including risk management strategies for your company and best practices to improve these strategies continually.
The facts in a nutshell
- ISO 27001 is a security standard that helps protect information assets by establishing an information security management system (ISMS).
- Risk management is a component of the ISO 27001 standard and aims to identify, assess, and treat risks in an ISMS through a consistent and repeatable risk management strategy.
- A good approach to risk management includes three components: a risk assessment process, a risk treatment plan, and review of residual risks.
- Different types of risks call for unique risk management strategies, including risk avoidance, risk reduction, risk transfer, risk retention and risk acceptance.
- Risk management is an ongoing process that must be maintained alongside the ISMS.
- To ensure successful risk management, companies should periodically re-evaluate their risk management strategies and develop new approaches to resolving underlying problems.
In this article
- What is ISO 27001 risk management?
- What are some of the risk management strategies that companies can adopt?
- What do you need to establish a strong risk management strategy?
- What are the best practices for ISO 27001 risk management?
- How can DataGuard support you with effective risk management strategies?
To start, let’s understand the full scope of ISO 27001 risk management.
What is ISO 27001 risk management?
ISO 27001 is a security standard that helps to protect your information assets by establishing an information security management system (ISMS). This system needs regular maintenance and continuous improvement for the best results, which is where risk management comes in.
Risk management is a component of the ISO 27001 standard and aims to identify, assess, and treat risks in your ISMS. Its main goal is to help companies make informed decisions about information security risks through a consistent and repeatable risk management strategy.
A good approach to risk management includes the following three components:
1. Risk Assessment Process:
This process involves identifying and assessing information security risks that may affect your company’s information assets. The risk assessment process includes:
- Identifying assets and threats
- Identifying vulnerabilities
- Assessing the likelihood and impact of each risk
- Determining the risk level
- Identifying risk owners and their responsibilities
2. Risk Treatment Plan:
Once the risks have been identified and assessed, developing a risk treatment plan is next. This outlines the actions needed to reduce, mitigate, transfer, or accept the risks. The risk treatment plan includes:
- Risk treatment options
- Prioritisation of risks
- Implementation of risk treatment measures
- Monitoring and reviewing of risk treatment measures
3. Review Residual Risks:
The residual risks are the risks that remain after the risk treatment plan has been implemented. These residual risks should be reviewed to ensure they are within your company’s risk tolerance. The review of residual risks includes:
- Documenting residual risks
- Reviewing residual risks regularly
- Adjusting the risk treatment plan if necessary
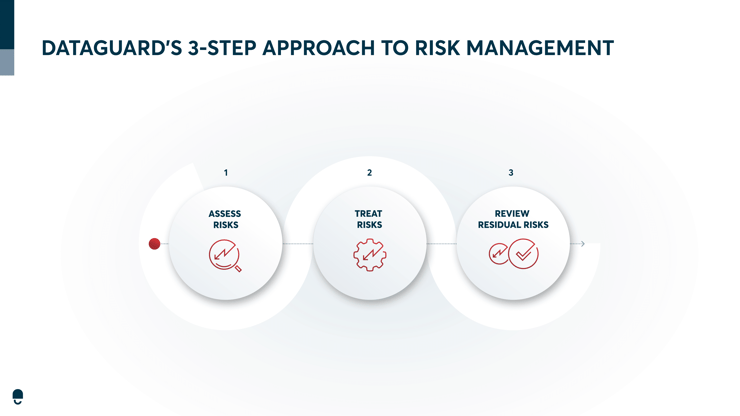
Risk management is a process that must be maintained alongside your ISMS. To do this and ensure successful risk management, you have to adopt a strategy.
What are some of the risk management strategies that companies can adopt?
Different types of risks call for unique strategies when it comes to risk management. Not all potential threats need the same response.
The choice of risk management strategy for your company depends on the company's goals, size and security needs. Once you have identified the best strategy, you can start implementing its components.
Here are some methods that you can use to mitigate potential threats in your company:
Strategy 1: Avoid
To mitigate or eliminate risk, people often take steps to ensure that the risk never occurs at first place. It involves identifying and evaluating information security risks and taking steps to eliminate or avoid them entirely. Risk avoidance is considered the most effective risk management strategy as it eliminates the possibility of negative consequences associated with the risk.
However, risk avoidance may not always be feasible or practical because there may be situations where the potential benefits of an activity outweigh the associated risks. In such cases, the organization may need to employ other risk management strategies, such as risk reduction, risk transfer, or risk acceptance.
Example: A company may choose to avoid using certain software or technologies known to be vulnerable to cyber-attacks, instead opting for more secure alternatives.
Strategy 2: Mitigate
Reducing or mitigating risks requires action to reduce the impact or likelihood of occurrence. Risk management aims to minimise potential negative outcomes to a tolerable or residual level. For financial reasons, most companies try to minimise risk wherever they can. You may reduce the impact of risks by adopting tight safety measures, diversifying your company's operations, or building up internal controls.
Example: A company may implement firewalls and antivirus software to reduce the likelihood of a cyber-attack or develop a disaster recovery plan to minimise the impact of a natural disaster.
Strategy 3:Transfer
By shifting responsibility for potential losses to other parties, companies can withstand economic crises. They can pool their risks with other parties, like employees, contractors, partners, or insurers. Business risks that are less likely to occur but would have a large financial impact if they did occur are ideally suited for risk transfer.
Example: A company may purchase insurance to transfer the risk of financial losses from a natural disaster or product liability claims.
Strategy 4: Accept
Risk acceptance is a way of dealing with risk by acknowledging it and choosing to live with the consequences of the risk without taking any action to transfer or avoid it. This means that an organization is willing to tolerate the potential negative outcomes of a risk because the cost of mitigating or avoiding the risk may be too high or because the risk is not severe enough to warrant further action.
Risk acceptance is a conscious decision to prioritize resources towards managing higher-priority risks and not to allocate resources to manage a risk that can be tolerated.
Example: A company operates a manufacturing plant and accepts the risk of occasional accidents and defects. Instead of investing in additional safety measures, the company allocates resources towards other aspects of the business. However, after experiencing a series of incidents, the company re-evaluates its strategy and implements additional safety measures to reduce the likelihood of future incidents.
What do you need to establish a strong risk management strategy?
An ISO 27001 risk management strategy needs certain components to stay compliant with the standard and better protect your data. They are:
- Establishing a strong ISMS
The foundation of successful ISO 27001 risk management is establishing an effective ISMS. It involves creating policies, procedures, and controls to manage information security risks and comply with the standard. An effective ISMS should involve all stakeholders in your company and be integrated into your company’s overall management system. - Informed decision making
Effective risk management requires informed decision-making. This means considering all relevant information when making decisions about risk treatment. It includes assessing the likelihood and potential impact of risks and considering your company’s risk appetite and tolerance. - Creating an effective risk assessment
Risk assessment is the process of identifying, analysing, and evaluating risks to the confidentiality, integrity, and availability of information. To create an effective risk assessment, it is important to use a structured approach that takes into account all relevant threats, vulnerabilities, and impacts. - Creating an effective risk treatment plan
A risk treatment plan is a document that outlines the controls and strategies that will be used to manage identified risks. In this document, risks should be prioritised and balanced according to treatment costs and benefits. - Selecting appropriate security controls
Security controls are measures that are used to manage information security risks. The ISO 27001 standard gives a comprehensive list of security controls from which you should select the appropriate controls for your company’s risks. - Ensuring business continuity
Effective ISO 27001 risk management ensures business continuity in the face of potential disruptions. It involves developing and implementing a business continuity plan that outlines the processes and procedures that will be used to maintain critical business operations in the event of a disruption.
As mentioned before, risk management is a continuous process. Once your strategy has been implemented with its relevant components, you need to work on keeping it up-to-date and relevant to risk management best practices.
What are the best practices for ISO 27001 risk management?
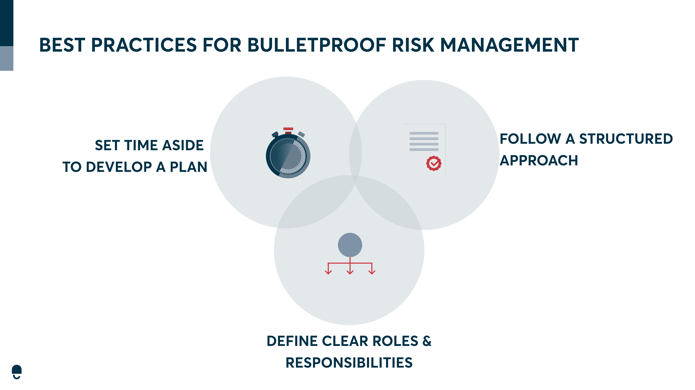
Implementing risk management best practices can help treat your information security risks effectively and ensure that risks are minimal in the future. Here are 7 best practices you can follow:
- Set time aside to develop a plan: Developing a risk management plan requires careful consideration and collaboration between stakeholders. You need to set aside enough time to develop a comprehensive risk management plan that aligns with your company’s objectives.
- Follow a structured approach: A structured approach ensures that all risk management steps are completed and nothing is overlooked. It also makes the process consistent and repeatable.
- Define clear roles and responsibilities: This must be done for each stakeholder involved in the risk management process to help them understand what their role in this process is. You should also ensure that everyone is held accountable for their responsibilities.
- Regularly review and update your ISMS: Risk management is not a one-time activity. You should regularly review and update your company’s ISMS so that it remains effective and aligned with business objectives.
- Conduct thorough employee training: Employees play a critical role in managing information security risks. Conducting thorough training on information security policies, procedures, and best practices makes everyone aware of their responsibilities so they can actively participate in risk management.
- Continuously monitor and measure performance: This is mainly done to identify areas for improvement. Key performance indicators (KPIs) like the number of identified risks, time to resolution, and risk reduction can help you track progress and measure the effectiveness of your risk management strategies.
- Engage with third-party vendors responsibly: Third-party vendors can pose a threat to your company’s information security. So, it’s important to engage with them responsibly by conducting a thorough risk assessment, establishing clear security requirements, and monitoring their compliance with security standards.
Creating an ISO 27001 risk management strategy is not an easy task. There are processes and tools that you may not be familiar with, which is why DataGuard has built a risk management platform to make it easier for you.
How can DataGuard support you with effective risk management strategies?
DataGuard can help you through our risk management platform, which allows you to:
- Take charge of your risks and minimise their negative effects. The platform provides a visual representation of your primary risks and vulnerabilities, helping you to prioritise which risks to address first.
- Manage all the relevant information about each risk, including its description, cause and impact, and keep track of all stakeholders involved in the project.
- Achieve a consistent and comparable evaluation of the risks your company is facing.
Looking to protect your assets and minimize risk? Feel free to contact our in-house experts today.
ISO 27001 risk management is critical for companies looking to keep their data safe and stay ahead of the curve. To create a risk management strategy that suits your business goals, you must understand what components are mandatory and how to adopt them into existing or unique strategies.
Following risk management best practices is a good way to stay up-to-date and keep your strategy relevant over time. Our experts at DataGuard can help you build a risk management strategy ideal for your company and provide the necessary tools to manage and improve your strategy over time.










