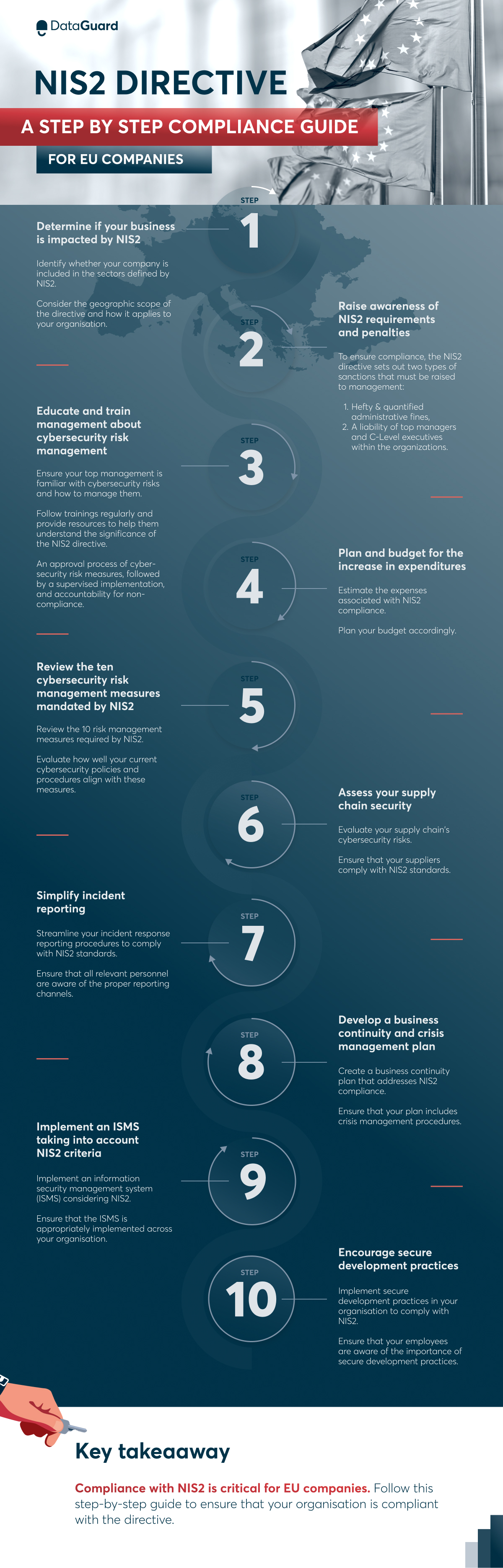
The NIS2 Directive: A step-by-step compliance guide


About the author
Don’t miss these topics:
Related Articles

2 Min
Microsoft and CrowdStrike outages: A wake-up call for cybersecurity?
Understand Microsoft outages and their cybersecurity implications. Learn about the causes, the impact, and get access to expert help if you need it.
Read more
5 Min
Why information security risks are business risks
Cyber threats blur the lines between information security & business risks. See how this impacts your finances, operations, compliance & reputation.
Read more
7 Min
Cyber security: Protect your most critical assets first
Learn how to identify your organisation’s critical assets and why you should protect them first, implementing a strategic approach and proactive measures.
Read more
4 Min
Risk mitigation consulting and services
Improve corporate governance and ESG priorities with Risk Mitigation Consulting. Utilize advanced analytics for tailored and proactive risk management.
Read more
7 Min
Information security services
Protect data, networks, and systems from cyber threats with Information Security Services. Enhance security with proactive monitoring and compliance.
Read more
4 Min
Information security risk management framework
Manage and mitigate security risks with the Information Security Risk Management Framework (ISRMF). Enhance risk visibility and streamline assessments.
Read more