The healthcare sector is now one of the most targeted sectors globally. According to research conducted by Check Point Software Technologies, the average global weekly attacks rose by 7% in 2023 in comparison to the corresponding period in 2022, with each organisation facing an average of 1,248 attacks per week.
The research also notes that this represents a considerable rise of 22% compared to the previous year. This also means healthcare has become the third most targeted industry in 2023.
Digital threats to healthcare providers also include operational disruptions, issues with medical devices, costly data breaches and theft of intellectual property -ample reasons to take a preventative approach to risk management.
What is risk management in healthcare?
Risk management is identifying and addressing information security risks that your healthcare company or organisation may encounter. The goal is to become aware of the risks your company is exposed to (for example, cyberattacks). While also making informed decisions to keep ensure operations and assets remain safe and secure.
In healthcare, this consists of complicated clinical and administrative systems and processes to identify and address risks related to the entire company or organisation. As healthcare providers handle an increased amount of digital data and payment systems become more digital, the fiscal and legal risks are no longer on the patient side; they are shifting and expanding to becoming an entire healthcare enterprise risk. Hospitals, healthcare facilities and companies are now adopting a more holistic, big-picture approach to managing risk across the entire organisation.
What are the principles of risk management in healthcare?
According to the World Economic Forum, the most common practice and principle within healthcare is the so-called zero trust security model. It's a principle that operates on 'never trust, always verify' — whether the information comes from an internal or external source. In general, it questions and segments which clinicians, doctors and healthcare staff should have access to what data.
Why is healthcare data at risk?
The three main reasons for an increased number of attacks, specifically in the healthcare sector, are:
- Many healthcare companies are using legacy software and systems with substantial security gaps.
- There’s a failure to adopt a preventative approach — aka no system or set of procedures for handling data and devices.
- Many healthcare providers are worried that the costs of risk management systems are simply too high and that it's going to exhaust internal resources.
Perhaps you're concerned that your company is one of them.
The true cost of avoiding risk management in healthcare
Risk management requires resources, which is often a reason companies put it on the long bench. Yet the cost of not managing risk is a hundredfold higher. Inadequate protection against attacks can cause your company to experience the following:
-
Operational disruptions
Security incidents can lead to lengthy downtimes, mainly due to ransomware attacks.
Productivity losses can be enormous. For example, hospital staff can’t access vital information, track records, etc. -
Issues with medical devices
If medical devices are targeted, things can get very serious very quickly. For example, the consequences of malfunctioning surgical or patient monitoring devices can cause a patient's well-being to become endangered within minutes.
It could even lead to having an impact on patients’ treatments, costly recalls, legal entanglements, and irreversible reputational damages. -
Costly data breaches
Data breach costs in the healthcare sector have increased by 42% since 2020. For the 12th consecutive year, healthcare had the highest average costs of all industries for data breaches. And the consequences of patient data theft go beyond legal repercussions and hefty fines; they touch the core of trust.
The stakes are high, to be frank: cyberattacks can cost you millions. Cybersecurity Ventures estimates global cybercrime costs will increase by 15% annually over the next five years. By 2025, they are projected to reach $10.5 trillion, compared to $3 trillion in 2015 — the largest transfer of economic wealth in history. -
Theft of intellectual property
Innovation is the lifeblood of medical technology. Therefore, intellectual property often represents one of the most valuable assets of a healthcare company. The financial damage is immense if stolen, and your entire company's future is threatened.
Risk management in healthcare needs to be preventatively managed before it's too late.
3 steps to risk management as a healthcare provider:
In healthcare, risk management can be broken down into a 3-step process:
- Identifying potential risks.
- Assessing the likelihood and impact of those risks.
- Taking actionable steps to address them.
Having risk management in place is the best way to prepare for the worst — yet hoping you’ll never have to put that plan into action.
Although the analogy of a picnic sounds simple, in reality, companies and systems are a lot more complex. Plus, you usually have several stakeholders involved.
This is why having an expert at your disposal who has faced these complexities time and time again — might make sense.
Navigating healthcare risks: A simplified 3-Step approach
The most effective process to manage risk is to:
- Identify and assess risk.
- Treat risks.
- Review residual risks.
Step 1: Identify and assess risks
First things first, you will want to identify and assess any risks that may be relevant.
Creating a risk map gives you the necessary tool to assess the likelihood and impact of risks. You can also determine the potential causes of these risks, which will in turn help you identify the impact of them.
In general, there are many methods to assess risk. Here are a few examples:
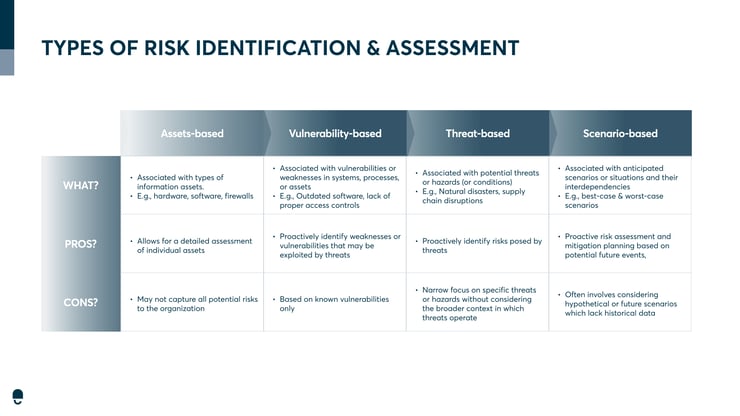
Although not necessarily common practice — scenario-based risk identification and assessment is the most effective way to manage risks. Not only does it consider past occurrences, but it also takes a preventive approach to risk management. This is a more holistic approach that covers all potential scenarios.
Step 2: Create a treatment plan
Once you have identified and assessed your risk, you will need to develop a treatment plan. This describes how you plan to treat and minimise the risk you identified in Step 1. In general, you have four treatment options which determine how you plan to address a risk. You choose a suitable option, define the desired risk level for each one and document the rationale behind your choices.
Step 3: Review residual risks
Last but not least, you need to identify what residual risks are present once you have identified and treated risks. These may be due to circumstances out of your company's control or simply be a risk your company is willing to take.
The process of establishing risk management within your healthcare institution or company can be time-intensive, expensive and frustrating — if you don't have the right tools and expertise at hand.
Risk management challenges you can face in healthcare (and how to overcome them)
If you decide to go down the route of managing your risk holistically, company-wide — you might face these complexities:
- No to little knowledge and expertise about risk treatment.
- A lack of in-house cybersecurity experts.
- Finding and hiring cybersecurity consultants may be too expensive.
- There may be confusion about which directives and laws to comply with (e.g., NIS2) and what is recommended in terms of which certification to obtain (ISO 27001:2013 or 2022).
- Your company might have low maturity of Information Security Management System (ISMS) and risk identification.
- Finding a starting point to establish risk management within your healthcare organisation.
- Maintaining and nurturing risk management in the long term.
Having information security experts at your side for guidance to overcome them might make sense. They can help streamline the process and overcome challenges by drawing on experience.
Risk management in healthcare
This article covers risk management in healthcare. Yet protecting your healthcare company can be done in two ways:
- Implementing reliable risk management.
- Or building an Information Security Management System.
Interested in finding out more? Read more about building an ISMS here: Information security management system: What it does and who needs it.


Unlock the Secrets to Successful Risk Assessment!
Dive deep into the "8 Critical Steps to Successful Risk Assessment" with our ebook. Don't leave your organisation's safety to chance.
Download now!









