Social engineering attackers are stepping up their game with the help of AI. When successful, such attacks can take a toll on a company's reputation and finances. If you're overseeing IT, it's crucial to strengthen defences against social engineering and recognise the susceptibility of human behaviour in the realm of cybersecurity.
How can companies defend themselves in an increasingly dangerous cyberspace? We sat down with one of our information security experts, Emrick Etheridge, Product Owner at DataGuard, to figure it out. Here’s what you can do as Head of IT.
What is social engineering?
Social engineering is a tactic used to trick people into revealing sensitive information or taking actions that can compromise security. It’s especially dangerous in companies, as it can cause reputational and financial damage.
We're all familiar with well-known examples of social engineering, such as phishing emails or text messages pretending to be our co-workers, business associates or official authorities.
However, these easily recognisable attempts have started to increase in sophistication through the use of AI. For example, using voice cloning and deep fakes to impersonate CEOs or other workplace leaders has become a common trick to get employees to divulge information, grant access to sensitive data or transfer money.
Want to stay one step ahead? Watch our on-demand-webinar about AI-led cyber threats and strategies on how to strengthen your cybersecurity in the evolving landscape of cyber threats: New cyber threats: your voice is my password
According to Emrick Etheridge, around 80 per cent of social engineering attacks can be fended off with technical tools. The remaining 20 per cent are due to human error. However, Etheridge is convinced: "When an employee falls victim to a social engineering attack, it's not the employee who has failed; it's often the company that has failed to train them properly”.
How social engineering works
Social engineering attacks, of which phishing is the most well-known form, exploit human emotions such as shame, fear, or greed to gain access to company information, sensitive data or money.
Emrick Etheridge explains that attackers and hackers manipulate these emotions and instincts to elicit desired responses from their victims. This is why social engineering attacks are known as "human hacking".
Cybercriminals often prey on the following emotions:
- Trust: They pretend to be from a trusted company or brand to gain easy access to company data.
- Fear and shame: Attackers pretend to be the CEO, for example, and use emotions of fear or shame to demand access to information by exerting pressure and preventing contact with superiors.
- Pressure: Using words such as "urgent" or "right now" plays on the emotion of time pressure.
- Helper instinct: Cybercriminals appeal to their victims' helper instinct by urging them to click on malicious links or visit certain websites.
Human emotions are, therefore, the weakest link in any organisation's defence against cyberattacks.
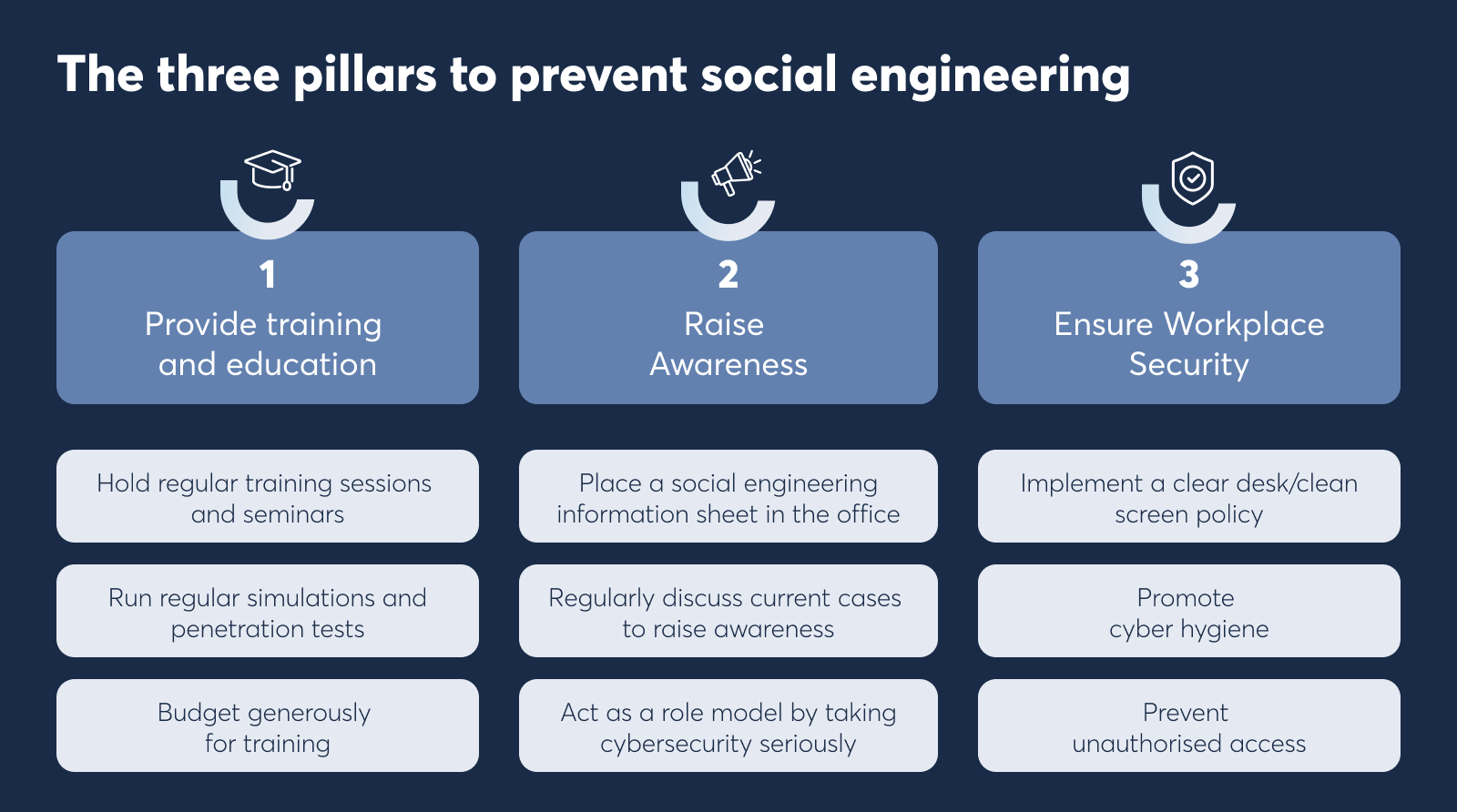
3 effective strategies IT leaders can use to minimise social engineering attacks
There are a few effective strategies you can use as an IT leader to minimise your organisation’s exposure to risks. Here’s what our expert suggests.
1. Provide training and education
Communication is vital for you as an IT leader, whether you are talking to board members or employees. Stress the importance of information security to your fellow managers and educate the rest of the company to identify and avoid risks.
Training your employees is one of the most critical steps in securing your organisation:
- Hold regular training sessions and seminars: Education is critical to cybersecurity.
- Run regular simulations and penetration tests: This will help you practice cyber hygiene and encourage security-conscious behaviour among your employees.
- Budget generously for training: Prioritise social engineering training for your employees as a top budget priority.
2. Raise awareness
Establish a culture where you regularly remind employees what to do in the event of phishing or other forms of social engineering.
Empowering your employees to be conscious and knowledgeable on the topic will lead to compliant actions across the organisation and reduce the risk of human error. Some examples of how to build this culture include:
- Place a social engineering information sheet in the office to keep employees aware of the issue and provide them with guidelines for action.
- Regularly discuss current cases to raise social engineering awareness and increase employees’ vigilance.
- Act as a role model by taking cybersecurity seriously and setting an example.
Cybercriminals mercilessly exploit negative emotions such as shame and fear in social engineering attacks. Emrick Etheridge, therefore, gives a clear recommendation for Heads of IT: “One of the most important rules in the fight against social engineering is: never shame employees who fall for an attack.”
Shaming people has a negative effect. They then no longer have the confidence to ask whether an email comes from their manager if they are in doubt. Cybercriminals like to play on this feeling. Therefore:
- Establish an open corporate culture: questions in case of doubt should always be allowed. Your employees should feel it is better to ask too many questions than too few.
- Promote your availability: Ensure employees contact you in uncertain situations to reassure themselves.
-
Increase your availability via different media: In the event of a social engineering attack, it is advisable for your employees to always contact you via a medium different from the one used for the attack. If someone has received an email supposedly from you, they should contact you via the Teams channel, for example.
You might also be interested: Cybersecurity trends that every IT Head should be aware of in 2024.
3. Ensure workplace security
Consider the physical aspect of the fight against social engineering. As Emrick Etheridge says: "Treat your workplace like your home".
- Implement a clear desk/clean screen policy: Create a culture where employees keep their desks clean, handle confidential information appropriately and do not leave sensitive data exposed.
- Promote cyber hygiene: Encourage employees to lock their screens and check if their colleagues' screens are locked when they leave the workplace. An effective approach to reinforce this practice is to hold individuals accountable for leaving their PC screens unlocked. This can be achieved through one-on-one communication, sensitively informing them that inadvertently leaving their PC unlocked could pose security risks. Frame the conversation in a non-shaming manner, emphasising the importance of preventing potential malicious use and creating a sense of personal responsibility.
- Prevent unauthorised access: This ensures employees know they should not let anyone enter the office without authorisation. "Someone with a ladder in their hand will be let into almost any building," Emrick Etheridge's joke warns of the ease with which unauthorised people can gain access. Make sure to raise awareness and train staff.
Education, friendly and open corporate culture and more cyber-savvy behaviour are crucial to your employees' resilience in a social engineering attack.
At DataGuard, we know how demanding it is for an organisation of any size to secure information and fight against social engineering attacks. If you want to hear more about what measures you can take to safeguard your organisation, reach out and have a chat with one of our experts.










