When a company loses data – either through theft, accident or a systems failure – the result is invariably financial loss, damage to their reputation, and even legal consequences. As the amounts of data, we deal with continues to rise alongside technological advances, so do the requirements necessary to keep it safe.
Information security is all about protecting data and corporate assets from unintentional own goal incidents as well as from prying hacker attacks.
This article covers:
- What is Information Security?
- Why information security is important- and getting more important
- Information Security is especially crucial in these industries
- Information Security objectives - the CIA triad
- The difference between data protection and information security
- Information Security vs. IT Security vs. Cyber Security
- Threats to Information Security
- Implementing information security with an ISO 27001-certified ISMS
- Responsibilities for information security
- Outsourcing information security
What is information security?
Information security or InfoSec for short covers all measures a company may take to protect their sensitive information.
While there are some international standards and norms that define the requirements for information security and the measures necessary to ensure it, there is no legally binding framework in place.
Thus, information security follows a more risk-based approach. Information security measures do not adhere to strict provisions, nor do they aim for iron-clad security. Instead, information security carefully weighs potential information security risks against their probability and level of potential damage.
Any company that wishes to have an effective information security infrastructure must strike a balance between risk exposure, damage potential, and risk-minimising measures that perfectly suits their individual situation.
Why information security is important – and getting more important
In recent years, numerous laws that directly deal with information security were put into place or updated. This in in part due to the high pace of technological progress and digitalisation that pose novel risks to today’s business community.
The most important such laws in the UK include the Data Protection Act 2018, the Data Protection, Privacy and Electronic Communications (Amendments etc) (EU Exit) Regulations (commonly called the “UK GDPR”) and the Privacy and Electronic Communications (EC Directive) Regulations 2003 among others.
At the same time, awareness is growing among consumers, B2B customer, investors, employees and other stakeholders. Investors subject companies to an intensive due diligence process, during which their information security is put under the microscope. Certification schemes such as ISO 27001 and TISAX® are playing an increasingly crucial role in the competitive marketplace for distributors and customers.
Information security is especially crucial in these industries
Each and every company should take information security seriously, regardless of the company’s industry or size. But the topic is especially crucial for highly software-driven and digital companies. This is also true for companies in highly regulated industries, such as the health care market for instance: The nature of the market demands that companies meet strict minimum standards for information security – for instance, to ensure doctor-patient confidentiality.
In the automotive industry, information security focuses more closely on the product: Vehicles are so complex and so many parties are involved in manufacturing that each product must pass through highly regulated approval processes before it can take to the roads. This means that all the actors involved in the supply chain must meet the requirements, without exception.
Information security objectives – the CIA triad
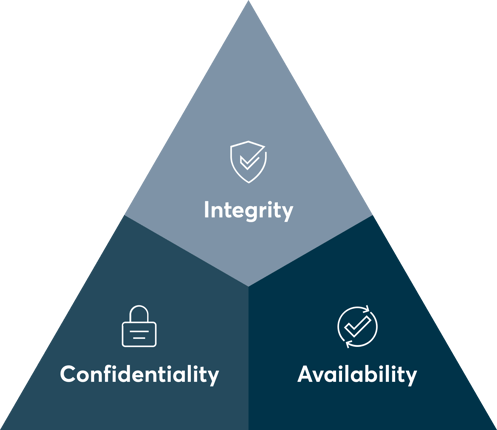
The three objectives of information security are:;
- Confidentiality
- Integrity
- Availability
You might have already heard somewhere about the CIA principle or “CIA triad”. The three letters of the acronym are taken from the three objectives of the protection paradigm listed above.
When you implement protective measures for information security, they should always follow at least one of these objectives.
|
Objective |
Description |
Measures |
|
Confidentiality |
Information must be protected from unauthorised access by third parties. Who is authorised must be clearly defined. |
|
|
Integrity |
Information must not be changed unintentionally or by unauthorised parties. In this context, integrity primarily means protection against unintentional changes. Unintentional changes to data are more likely occur due to defective systems and processes than through human error. |
|
|
Availability |
A technological infrastructure must be built that makes data and information relevant by preventing system failures. If data is lost, operationality must be restored as soon as possible. |
|
The difference between data protection and information security
As described above, information security focuses on protection information and corporate assets. A legal framework is only in place for certain special cases.
Data protection on the other hand refers to the protection of personal data. Here the focus is less on the information itself as on protecting the people behind the data. Since Brexit, the UK-GDPR (practically identical to the EU’s GDPR) forms the legal basis for data protection in the UK, tailored by the Data Protection Act 2018.
Despite the fundamentally different perspective that InfoSec and data protection take on the protection of information, the two concepts have much in common. Leveraging their synergies will save you a lot of time and work.
Information Security vs. IT security vs. Cybersecurity
The term IT security is sometimes misleadingly used as a synonym for information security or cybersecurity. The difference: Information security focuses on the protection of information. The information itself is the asset. It exists independently of IT or cyberspace and requires protection in all its forms – whether as a file bursting with printouts or unique company know-how in your employees’ heads.
IT security refers to the IT infrastructure: Everything from computers, servers, clouds and even wiring and the like must be secure and protected from access by unauthorised persons. The purpose of an IT system is to transport and process information.
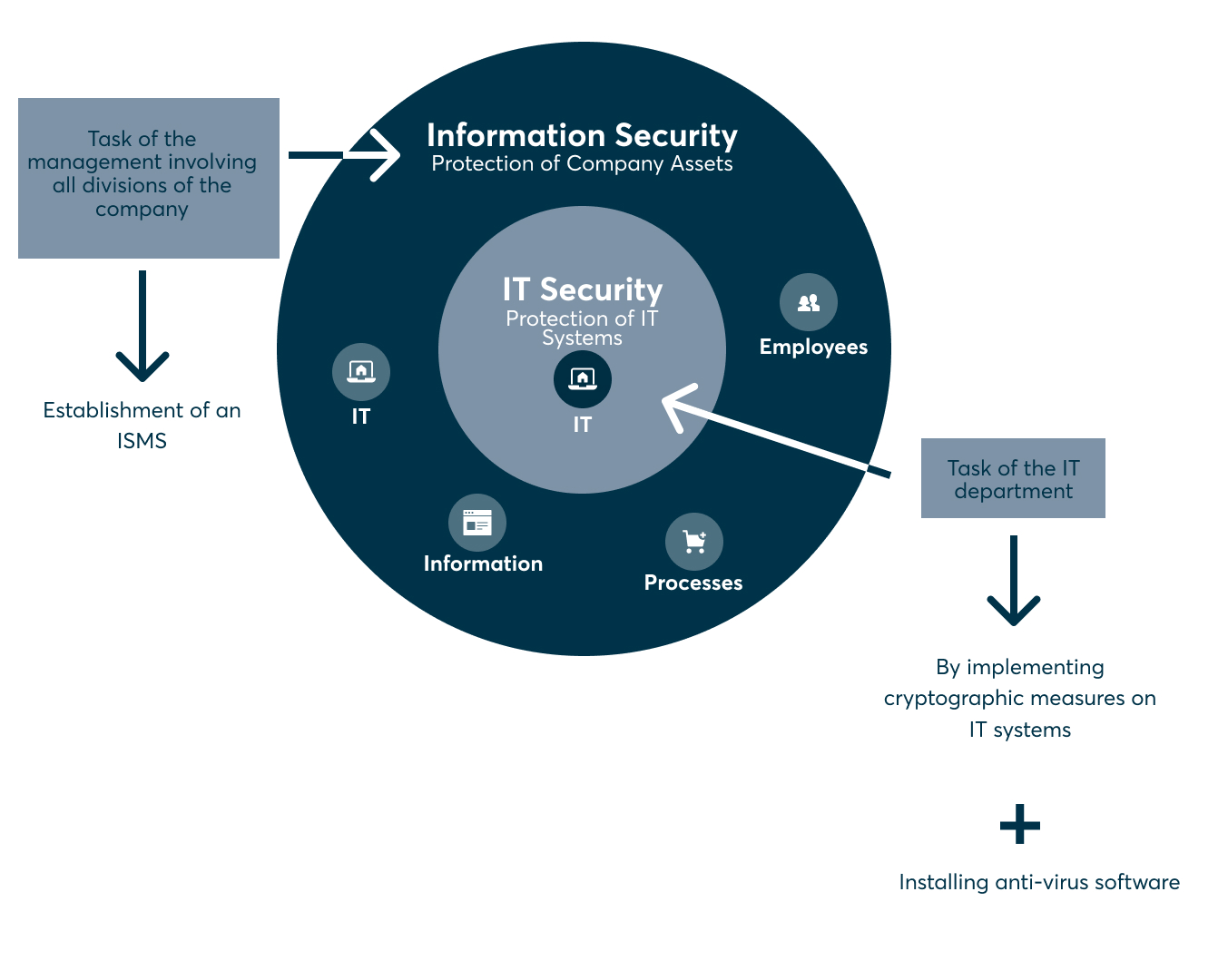 Finally, cybersecurity should be understood as a branch of IT security. It pertains to the protection of information in cyberspace, i.e., information security on the web.
Finally, cybersecurity should be understood as a branch of IT security. It pertains to the protection of information in cyberspace, i.e., information security on the web.
Threats to information security
When they hear “threats to information security”, most people immediately think of cyberattacks, organised crime and espionage. And it’s true: Criminal attacks – in particular on digital systems – pose a serious threat with far-reaching consequences:
In 2020/2021 alone, theft, espionage and sabotage cost German companies 223 billion euros. In 2018/2019, the figure was only 103 billion euros. According to a Bitkom survey, nine out of ten responding companies had been directly affected by cyberattacks.
But it’s not just bad actors, even a company’s own employees represent a threat to information security, intentionally or by accident. The same is true of defective systems, processes, and physical threats through natural disasters.
Threats to information security include:
1. Physical threats such as a fire in a data centre
2. Threats through employees such as theft or negligence
3. Threats through processes and systems such as out-of-date software without the necessary security updates and misconfigured or incorrectly integrated IT systems
4. Threats through cyber criminality such as ransomware attacks, phishing and social engineering
Implementing information security with an ISO 27001-certified ISMS
If you want to protect your company from the threats we’ve discussed here, you don’t have to start at zero and think up measures to protect your information assets on your own. Instead, there are established best practices you can follow. In terms of information security, they are laid out by the international ISO 27001 standard. ISO 27001 provides a high level a; blueprint for building an information security management system (ISMS). An ISMS ensures transparency and predictable processes, making it easier for companies to calculate and control information security risks.
ISO 27001 is intended to be applicable to every company. This means the standard must remain highly abstract and general. An expert is needed to interpret the standard for your company’s requirements and translate it into both plain English and a manageable Road Map,, someone like a Chief Information Security Officer (CISO) or Information Security Officer (ISO).
There are many good reasons to implement an ISMS. For example, if your business operates in a largely unregulated market, you can stand out to target customers by adhering to strict standards for information security and thus gain a competitive edge. In any case, an ISMS will increase the value of organisations because without one, companies don’t have a clear overview of their own processes and information assets. When looking for investors, an ISMS will pay off instantly: Without one, it is possible to carry out a due diligence process to a limited extent only.
Responsibilities for information security;
An ISMS can only be successfully put into place if management backs the concept and makes the necessary resources available. In addition to funding, the responsibilities must be clarified. In large-scale companies, the responsibility for setting up and the ongoing optimisation of an ISMS falls to the Chief Information Security Officer (CISO) or the Information Security Officer (ISO).
The tasks of a CISO or ISO include:
- Implementing IT security, setting up an ISMS
- Certifying the ISMS to ISO 27001 or TISAX®
- Processing and managing information security incidents as well as setting up a business continuity management program.
- Choosing suitable methods and tools
- Staff training and information security awareness-raising activities
- Risk management and advising company management
- Communication between departments
Information Security Analyst, Information Security Officer and similar jobs are highly respected positions that often bring in a six-figure salary.
Depending on the company, the position of CISO can be filled by an internal employee or an external service provider.
Outsourcing information security
Not every company has the resources or the will to implement and manage information security. In some cases, the internal team might be overworked and overwhelmed by the heavy documentation load. Perhaps the team doesn’t have the right expertise for a certain project or fails a due diligence audit. When faced with challenges like these, it’s best to turn an external service provider for guidance.
The advantage: External services are quick to purchase, and the service provider’s experience means you skirt the timely onboarding process. A good provider will assign you a personal contact, your personal go-to for all the challenges your company faces with the know-how from past experience to overcome them.
Another win: It is more cost effective to hire an external service provider than to pay the salary for a full-time company position. At DataGuard, our customers pay just between 420 and 1700 pounds a month, depending on the complexity of their needs.
There are still some questions that you would like to get answered? Feel free to reach out to one of our experts.












