With rapid technological innovation as the norm, IT leaders and CISOs face many continuously evolving challenges. With the development of new AI technologies and the constant adaptation to enacted cyber laws and data protection policies, the information security requirements in professional services are complex and demanding.
We talked to Emrick Etheridge, Information Security Expert and Product Content Owner at DataGuard, to better understand this changing landscape.
This blog post will highlight the top 5 information security challenges facing professional services and how IT leaders can effectively address them.
1. Maintain customer confidentiality
Protecting sensitive customer data is one of the many crucial responsibilities of any CISO and represents the vulnerability of any service-oriented business. CISOs are responsible for overseeing all data, ensuring it's securely encrypted, and implementing necessary measures for data protection.
Particularly in larger organisations, ensuring that sensitive data remains protected from external and internal threats can be an immense challenge. Neglecting your security measures and exposing data can harm your organisation and your customers. "And then you can pretty much say goodbye to the possibility of winning larger companies with established brands in the future," notes Emrick Etheridge.
A worst-case scenario for any IT leader is losing or compromising sensitive customer data. Therefore, it is imperative to ensure that data is protected in accordance with the General Data Protection Regulation (GDPR) and other relevant regulations. By taking appropriate security measures, organisations can prevent sensitive information from falling into the wrong hands and seriously damaging their reputation and customer trust.
2. Educate employees on the Dunning-Kruger effect
The more cybersecurity-savvy people you have in your organisation, the more effectively your data is protected. Here, it‘s worth talking about the phenomenon known as the Dunning-Kruger effect, as it poses an often underestimated headache for CISOs and IT leaders.
The Dunning-Kruger effect illustrates how individuals with limited expertise in a specific area tend to overrate their abilities. It's tough to judge our own skills accurately.
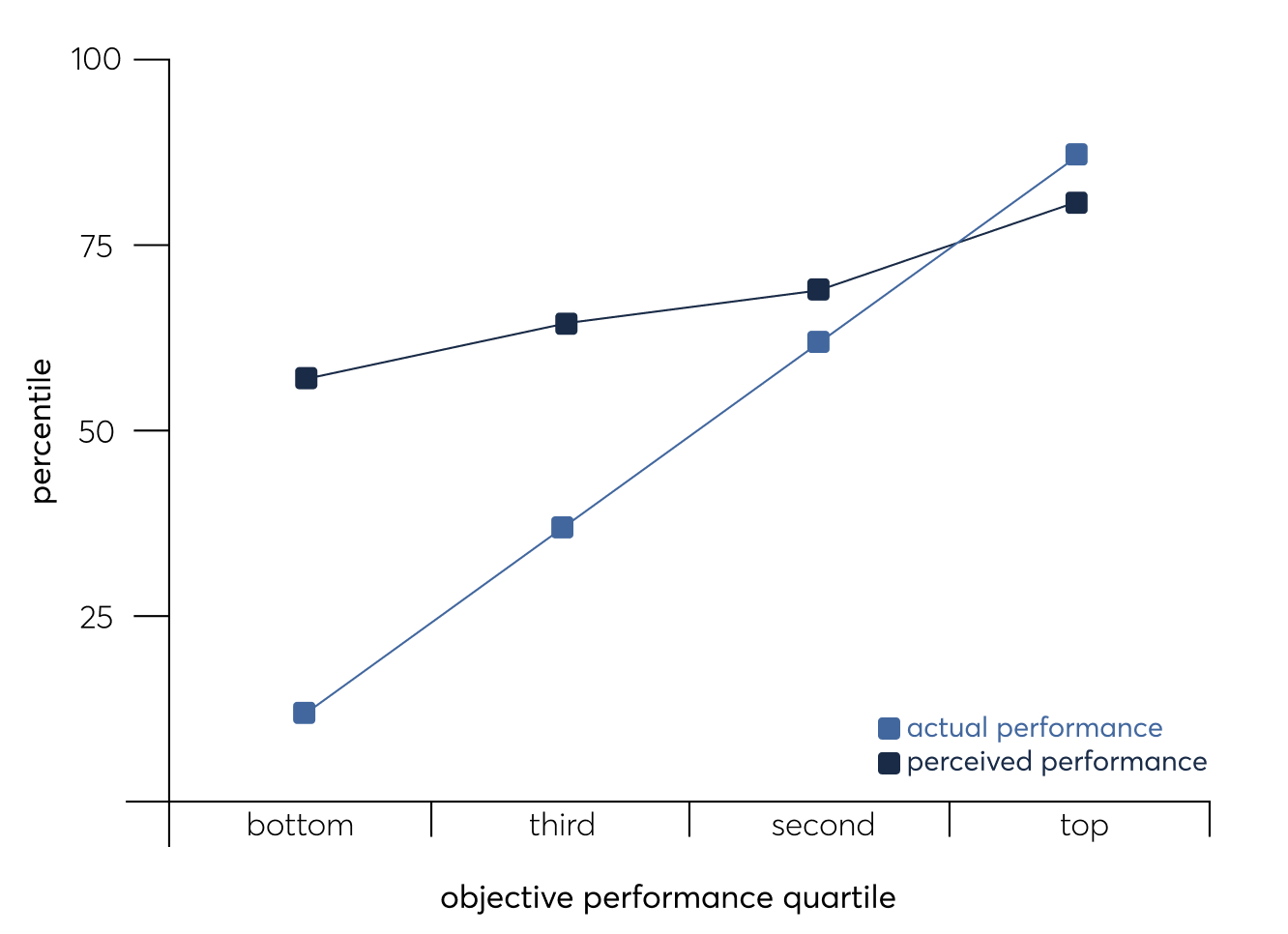
The Dunning-Kruger effect plays a vital role in cybersecurity. Employees with this mentality are more likely to ignore warning signs, such as those of a phishing attack, putting them at risk of falling victim to a cyberattack. "These employees can be just as dangerous as someone with no cybersecurity knowledge at all," says Emrick Etheridge.
Be aware of this effect and address it in your employee training. Cyber hygiene and the adoption of cyber-secure behaviours in the workplace are essential for any service-oriented business that wants to be prepared against attacks.
3. Take insider threats seriously
Termination, unfair treatment or greed - there are many reasons why employees might want to harm their (former) company, such as leaking data or initiating a cyberattack. The danger of insider threats is often underestimated, especially by junior CISOs who may have too much trust in employees. Trust is a good thing in itself. But when insider threats are consistently underestimated, they can be a real danger.
Based on a survey of global CISOs conducted in 2023, 30% of respondents identified insider threats as a significant cybersecurity risk to their organisations. So, beyond external threats, implement security measures for internal dangers as well.
One effective strategy for mitigating insider threats is establishing different access levels. "When it comes to sensitive information, I believe people should have different access levels, even if they do not need it immediately. It's better to have it and not need it than the other way around.”
This helps reduce the risk of insider threats and encourages employees to use their access rights responsibly. Emrick emphasizes that individuals are generally less likely to act maliciously if they have a certain level of access, as this increases their accountability. "In the UK, for example, employees are usually required to obtain a specific security clearance, such as SC clearance, to perform certain tasks, often in conjunction with the police". This practice could prove an effective way of minimizing the risk of insider threats.
4. Beware of “Script Kiddies”
The threat landscape has changed dramatically with the emergence of AI-driven criminal activity in cyberspace. Sophisticated forms of social engineering, such as phishing and exploiting easy-to-find vulnerabilities, are now common tactics that continue to increase.
GenAI tools such as ChatGPT play an important role in this development. They make it easier for attackers to spread deep fakes and convince employees to grant access to sensitive information.
Most importantly, AI helps hackers quickly identify and exploit the low-hanging fruit of any organisation. This makes it easier for inexperienced hackers, known as “Script Kiddies”, to launch attacks on your data. This is a major challenge for CISOs and IT leaders.
As an IT leader, ensure you stay on top by offering training, keeping the lines of communication open with experts, and educating your team about various phishing tactics. Raising awareness about the risks posed by AI-driven attacks is also crucial.
With AI, there's a chance to automate and enhance defences against cyber-attacks. That's why IT leaders must embrace AI and GenAI and amp up their knowledge in these domains. Make AI your ally and turn the tables in your favour. As a CISO, it's helpful to understand the hacker's perspective, including the motivations of script kiddies, to address these threats proactively.
You may also be interested: 4 cybersecurity trends every head of IT needs to know about in 2024.
5. Secure your supply chain
Cyberattacks exploiting supply chain vulnerabilities are escalating and significantly threaten your business. This was highlighted by the breach of IT service provider Kaseya, orchestrated by the REvil hacking group. In cases like this, hackers infiltrate corporate supply chains for extortion and economic espionage. The impact of such attacks extends not only to the targeted company, in this case, Kaseya, but also to numerous customers and their respective networks.
So, keep an eye on your internal security rules, but don't forget to check your suppliers' security too. Go through your contracts carefully to ensure your global data protection solutions follow local laws, especially with GDPR.
You might also be interested: Communicate with confidence: Empowering IT leaders to influence change.
To mitigate the risk of supplier security breaches, conduct comprehensive security assessments. For example, use supplier security questionnaires to verify that suppliers meet the required security standards. These measures are critical to building confidence in the supply chain and identifying potential vulnerabilities.
View this process as an ongoing exercise. Much like a car's MOT, suppliers' security should be regularly assessed to ensure they continue to meet security requirements; however, you would also not wait for your vehicle to go for an MOT before you did a service. In the same way you would maintain a car, you should also frequently ‘service’ your cyber security in your organisation in a preventative manner and not just a reactive one.
Now that you know the top 5 challenges, we realize that dealing with them will require time, resources, and effort. Feel free to reach out if you need any help improving your organisation's information security. We're here to help.










